Blog & insights

- 3 min read
- July 27th, 2023
Featured
Recent articles

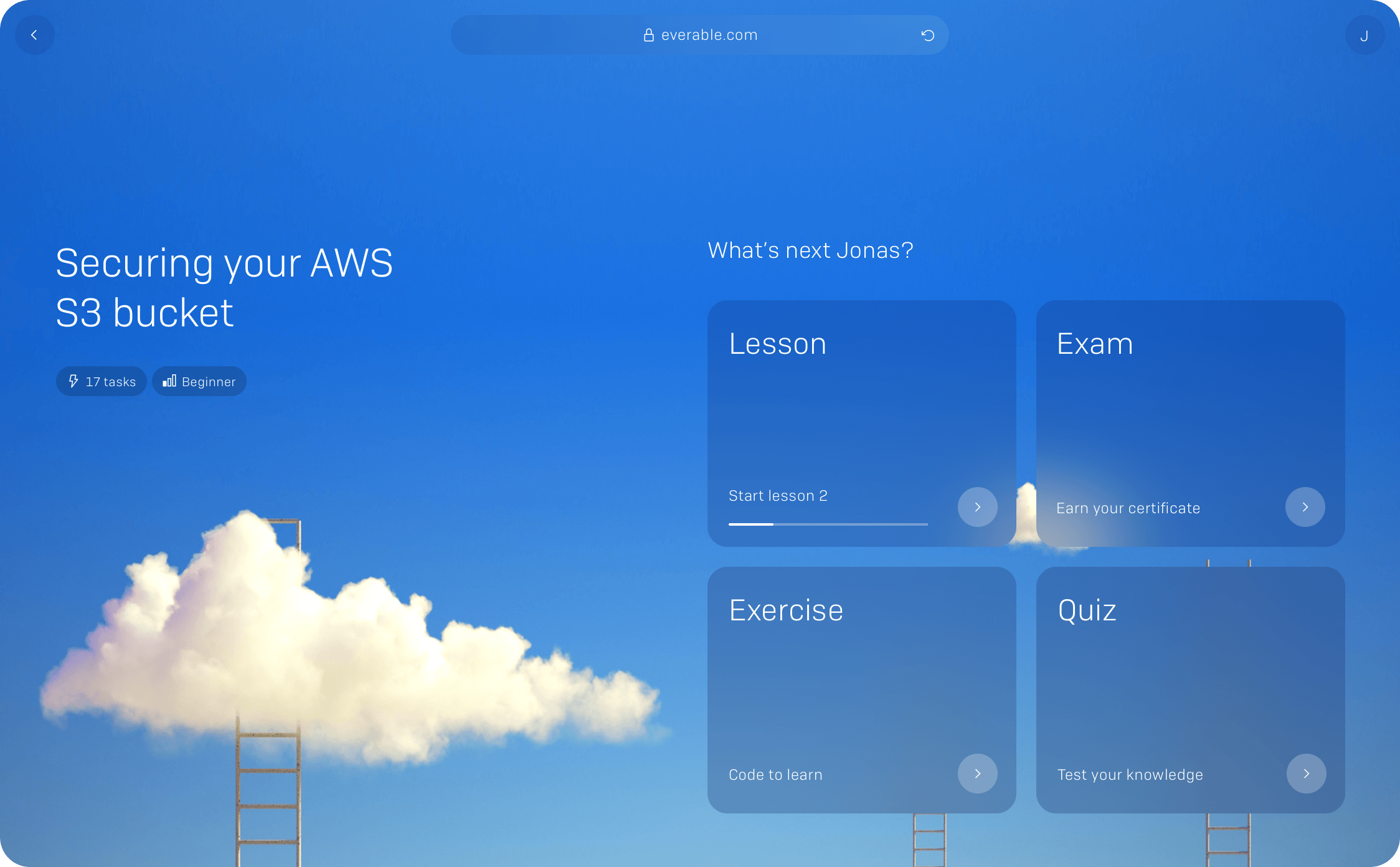
Applying Basic Principles for Secrets Management in Kubernetes Clusters
This article focuses on the often-overlooked area of secrets management in Kubernetes clusters. Kubernetes is an...
- 3 min read
- July 27th, 2023


Protect Your AWS Environment with Threat Detection and Monitoring
This blog focuses on the important topic of threat detection and monitoring in AWS. In this article, we'll introduce...
- 3 min read
- July 3rd, 2023


Why Security Education is Crucial for Organizations
In a world where cyber-attacks and data breaches are becoming more prevalent, it is essential that organizations...
- 3 min read
- June 19th, 2023

The Power of Defense in Depth for Protecting Your Digital Assets
Introduction:
- 2 min read
- June 2nd, 2023


The Importance of Shared Responsibility in Maintaining Security
In today's technological landscape, security is a concern for every company. A healthy DevSecOps culture involves...
- 3 min read
- June 1st, 2023


Maintaining Integrity in a Digital Landscape
In today's world, everything is becoming digital. Most of our data is stored and transmitted digitally, from finances...
- 3 min read
- May 15th, 2023


How the Growing Threat of DDoS Attacks impacts Availability
In today's world, where everything is connected to the internet, availability has become a critical concern for...
- 3 min read
- May 1st, 2023


Discovering Synergies: DevSecOps and Compliance
There’s a “need to raise the bar, and keep raising the bar because it’s getting riskier and riskier.” This is James...
- 3 min read
- September 21st, 2022


DevSecOps Skills Required for Transitioning your Organization
DevOps has witnessed a transformation in recent years. In the past, security was implemented in the final stages at the...
- 5 min read
- September 14th, 2022


10 Best Practices to Adopt DevSecOps within your Organisation
With the rise in the rate of cyberattacks over the past few years, the need to adopt security is increasing. Such...
- 6 min read
- August 20th, 2022


Try Everable today
Train, benchmark and improve cybersecurity skills across DevOps teams, all in one place